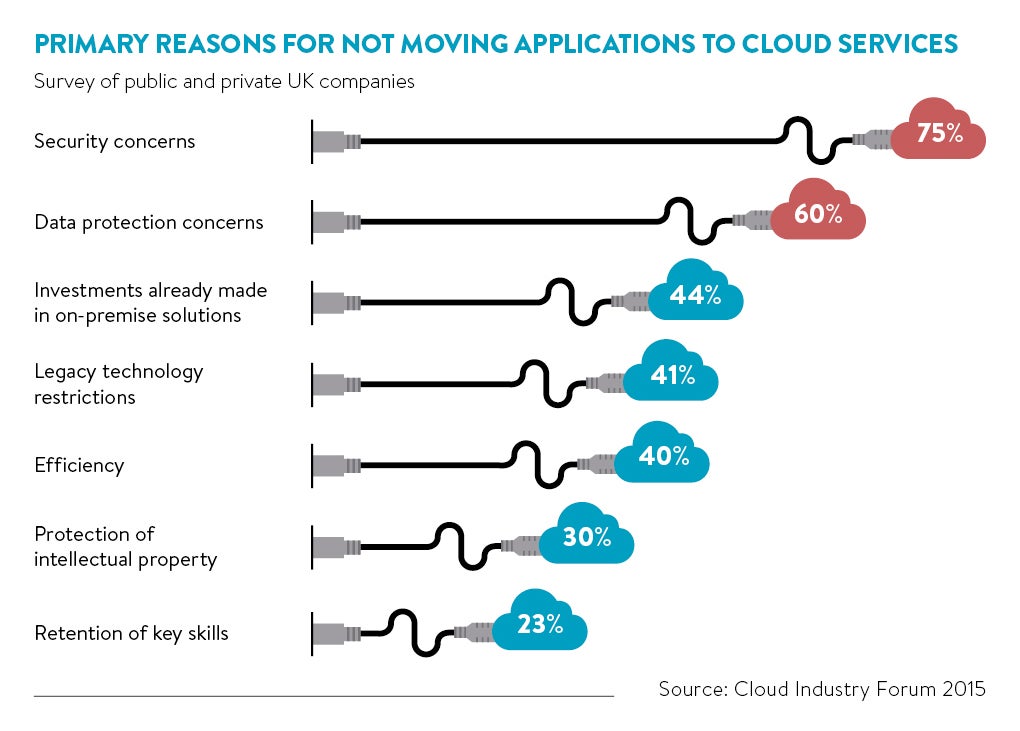
When hosting provider Rackspace commissioned Vanson Bourne to interview 500 decision-makers about cloud migration plans, the results suggested that security is a top-three motivator for moving to the cloud. This isn’t quite as encouraging as it first appears.
While reducing IT costs resonated with 61 per cent of respondents ahead of disaster recovery for 50 per cent, security was a distant third with only 38 per cent. That leaves 62 per cent yet to get the cloud security assurance message.
So why is convincing management that the cloud brings financial and functional benefits to the table so easy, but that it isn’t inherently insecure so hard?
“Security is a topic that is still not fully understood by many organisations as they prepare to migrate to the cloud,” says Simon Leech, chief technologist for security at Hewlett Packard Enterprise, “and it’s this uncertainty that plays on executives’ minds when they are assessing the viability of cloud.”
Risk is usually the reason put forward when organisations are both discussing, and delaying, cloud migration; they can outsource the operation of the public cloud, but it’s impossible to outsource the risk to the business itself. After all, should a breach occur at the cloud service provider that results in customer data being compromised, it’s not the provider’s reputation that gets damaged.
The truth is that responsibility for data security sits with the chief information security officer wherever that data may reside. Yet there is no great panic about the risk of datacentre insecurity or on-premise insecurity when perhaps there should be. After all, most data breaches that made the headlines last year involved traditional on-premise IT rather than the cloud. That cloud-based data continues to dominate the insecurity debate can be explained by one word – control.
John Godwin, director of information assurance and compliance at Skyscape Cloud Services, blames a lack of security education for this continuing corporate confusion. “The reality is cloud infrastructure does not inherently make cloud services and software offerings any more or less secure,” he says. “But most organisations feel more comfortable if they have absolute control over their data even if, in reality, it’s less secure.”
This argument would appear to be confirmed by the Vanson Bourne survey which suggested 84 per cent of UK chief information officers (CIOs) worry that the cloud causes them to lose control over IT. It’s a statistic that Mr Leech puts down to an increase in what’s known as “shadow IT”. Such unauthorised hardware, software or services can weaken the overall security posture.
“End-users may find it easier to order a cloud service on a credit card,” he explains, “rather than wait for the organisation to go through the process of deploying the service they need.”

Rob Lamb, cloud business director for UK and Ireland at EMC, warns: “Bypassing IT policies and controls, or uploading data into unsanctioned cloud instances, not only aligns to the CIO’s loss of control concern, but also increases the risk of a customer-originated security failure.” It’s something the Gartner Top Strategic Predictions for 2016 and Beyond report predicts will account for 95 per cent of all cloud security failures up to 2020.
Javvad Malik, a security advocate at AlienVault, is inclined to agree with Gartner that the risk comes primarily through the user “for not understanding and acting upon their responsibility”. Mr Malik puts this down to a mentality AlienVault sees a lot often among smaller organisations.
So, what can be done to mitigate the cloud security risk? Raj Samani, chief technical officer for Intel Security in Europe, recommends that when migrating to the cloud a business should first ensure it knows the value of its data.
“Identifying information assets ensures that only data which is suitable to be moved to the cloud makes the transition,” Mr Samani advises. “Organisations must also recognise that traditional security models no longer apply.” Just as shops barcode each individual product instead of relying on a perimeter security guard to prevent theft, cloud security must focus on protecting the data itself, not the data location.
When it comes to risk mitigation in the cloud, the sharing of responsibility for security is to be ignored at your peril. “Cloud service providers are responsible for physical and network security, while users are responsible for securing the data they are putting into the cloud,” says Pravin Kothari, chief executive at CipherCloud.
[embed_related]
The problem is that too many organisations assume that signing a cloud contract shifts security responsibility to the provider. “This assumption creates a lot of unnecessary risk because the customer at that point doesn’t take the necessary steps of building data-level protection, like encryption, tokenisation and access policies that can secure information in the event of a network breach,” says Mr Kothari.
Uncontrolled adoption of public cloud services – the shadow IT problem – is a genuine security risk and one that raises both regulatory compliance and data protection concerns, says Terry Greer-King, director of cyber security at Cisco UK.
“The most effective way to mitigate sources of risk when it comes to cloud computing is to adopt an integrated security policy that ensures visibility and control across the entire network, its access points and known or unknown applications,” says Mr Greer-King. Adopting this “security as a process” approach enables organisations to determine effectively the right cloud services for the business.
DISPELLING MYTHS ABOUT THE CLOUD
Understanding the issues that really exist, wherever your data resides, is key to good security. So it’s time for security experts to debunk a few persistent cloud security myths.
 1. The cloud is less secure than an on-premises solution: “Not true. Cloud still has physical anchors in the form of datacentres. Most cloud service providers (CSPs) have better physical security for their datacentres than most companies have for their own facilities,” says Pravin Kothari, chief executive at CipherCloud.
1. The cloud is less secure than an on-premises solution: “Not true. Cloud still has physical anchors in the form of datacentres. Most cloud service providers (CSPs) have better physical security for their datacentres than most companies have for their own facilities,” says Pravin Kothari, chief executive at CipherCloud.
 2. The CSP is responsible for securing your data: “When you outsource IT operations to the cloud, you don’t outsource your risk. End-responsibility for data lost in a breach always rests with the organisation – and in some cases the individual – that owns the data,” says Simon Leech, chief technologist for security at Hewlett Packard Enterprise.
2. The CSP is responsible for securing your data: “When you outsource IT operations to the cloud, you don’t outsource your risk. End-responsibility for data lost in a breach always rests with the organisation – and in some cases the individual – that owns the data,” says Simon Leech, chief technologist for security at Hewlett Packard Enterprise.
 3. Users in the same cloud can attack each other: “A common concern is that attacks from one customer to another are easier because everyone is using the same service. But it’s extremely difficult for one virtual machine to attack another. Most providers go further than the basics in ensuring that all layers of a virtual machine are isolated from each other,” says David Barker, technical director and co-founder of 4D.
3. Users in the same cloud can attack each other: “A common concern is that attacks from one customer to another are easier because everyone is using the same service. But it’s extremely difficult for one virtual machine to attack another. Most providers go further than the basics in ensuring that all layers of a virtual machine are isolated from each other,” says David Barker, technical director and co-founder of 4D.
 4. Data in the cloud can be located anywhere as long as it’s encrypted: “Encrypted data is still subject to data protection law if the encryption can be reversed and the data personally identifiable. You need to understand which country and data protection legislation is applicable to your data, whether encrypted or not,” says John Godwin, director of information assurance and compliance at Skyscape Cloud Services.
4. Data in the cloud can be located anywhere as long as it’s encrypted: “Encrypted data is still subject to data protection law if the encryption can be reversed and the data personally identifiable. You need to understand which country and data protection legislation is applicable to your data, whether encrypted or not,” says John Godwin, director of information assurance and compliance at Skyscape Cloud Services.


DISPELLING MYTHS ABOUT THE CLOUD






