There are two main points to make about security of the internet of things. The first is that it’s terrible. Abysmal. This is a fact. No one disputes it. “IoT security is in the dark ages,” is how Ken Munro of cyber security company Pen Test Partners puts it.
“Many IoT devices are hitting the shelves that simply aren’t secure and can easily be compromised and used to launch attacks on the home network or the mobile device they connect over,” he says.
Mr Munro’s company has made a name for itself by hacking internet-connected devices. It has hijacked kettles in order to gain control of a home network. It has demonstrated how to watch CCTV footage without the owner’s consent. It’s depressingly easy. A survey by HP suggested 70 per cent of IoT devices are insecure. Even amateur bunglers can hijack some mainstream products.
The second point is that consumers don’t seem to care. At least, not yet. Despite the deluge of bad publicity about security, the industry surges on.
Thieves could steal driverless cars from garages – they’ll just drive off, never to be seen again
The question for the future is when this carefree attitude will turn sour. Consumers are blasé today. In the future, when it becomes clear that hackers and bored teenagers alike are seizing control of IoT devices for nefarious ends, the mood may change. And the industry needs to take action before that negative reaction becomes a threat to its viability.
We’ve already had a few warning shots. Last July, Fiat Chrysler recalled 1.4 million vehicles after two security researchers demonstrated how to hack the Uconnect dashboard computer system of a Jeep Cherokee. The hack provided wireless control over the steering, transmission and brakes. The incident triggered a rash of articles in newspapers and magazines speculating about the harm that could be done in a similar attack.
At the DEF CON hacker conference in Las Vegas, a hacker by the handle Zoz said: “I’m a huge fan of unmanned vehicles. I love robots. I think they’re the future. But, like everything else humans ever made, it’s going to get hacked.” The possibilities for mischief are terrifying. Terrorists could use cars as missiles to smash into targets. Thieves could steal driverless cars from garages – they’ll just drive off, never to be seen again.
The vulnerability of the home networks
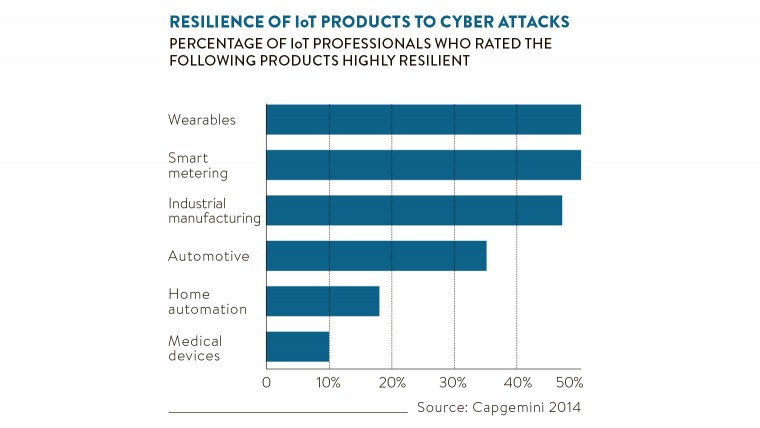
Home networks are the current focus of hackers. Not a week goes by without a fresh vulnerability being disclosed. Research teams amuse themselves by finding the most improbable angle of attack.
Kaspersky Lab found a way to exploit a coffee machine to gain control of a home wi-fi network. Canadian privacy lobbyist Open Effect wrote a report on how to snaffle data from personal fitness devices. There have been hacks on smartfridges, internet-connected kettles and children’s toys.
[embed_related]
Research suggests consumers are slowly waking up to the danger. A survey by Fortinet suggested 68 per cent of homeowners are concerned about a data breach from a connected device. Fortunately, sales do not yet seem to have been harmed.
So what does the industry need to do to guarantee a satisfactory level of security?
According to the leading names in the industry, it seems there is a huge amount of work to do.
It starts with the industry thinking about security from product inception. This will be a big shift. “Unfortunately, security is often an afterthought,” says Chris Boyd, an analyst at Malwarebytes. “This is largely because it’s expensive to ensure a reasonable standard of protection on a product, but also because there still seems to be a genuine lack of knowledge around basic cyber security precautions for IoT device manufacturers.”
Cyber security precautions
The industry needs standards. Simon Heron, chief technology officer of Redscan, points out that the current situation is a bit of a shambles. “There are many IoT protocols in the market, such as advanced message queuing protocol (AMQP), digital data service (DDS), the constrained application protocol (CoAP), ZigBee and others,” he says.
“These do not lend themselves to a coherent security posture, especially as the protocols are being extended to cope with the requirements of implementation.”
Often even simple things are missing. Passwords are too short or don’t lock accounts when multiple attempts are made, making it possible to crack via a brute force attack. Mr Heron points to the Nissan Leaf electric car, which had a vehicle identification number stencilled on the windscreen. “It was only the last five digits of this number that varied, so an unattended car could be controlled remotely,” he says.
Devices are often on the same network. So when one device is hacked, the whole ecosystem is exposed. The solution? “Network segmentation is a practice we need to start seeing in homes,” says Paco Hope, principal security evangelist at Cigital.
“It should impose isolation so no device on that network can see any other device on the network and they should not be able to connect to any devices on the home wi-fi networks in the house. And frankly, a third ‘guest’ network for visitors and their phones would be a good idea.”
Firewalls will play a big part. Manufactures should offer bounties to hackers, just as Facebook does to white-hat, ethical hackers.
In the end, consumers may hold the solution. “Given the apathy of vendors, the user currently needs to be proactive when buying an IoT device,” advises Mr Munro of Pen Test Partners. “Ensure you change the default settings and configure the device securely by implementing a PIN; don’t publicise your purchase online; use a unique password for your user account, not the same account passwords as you use for other sites; and, in the case of RFID [radio-frequency identification] tech, shield the device when not in use.”
Consumers should only buy from vendors who take security seriously. This revolution is too exciting to be halted by hackers and teenage saboteurs. The companies who understand that should be rewarded with your custom. And those that don’t – good riddance.