 When Tesco Bank fell victim to a cyber breach, hackers were quick to boast on the dark web about it being a cash cow and how they were cashing out £1,000 each week without anyone noticing.
When Tesco Bank fell victim to a cyber breach, hackers were quick to boast on the dark web about it being a cash cow and how they were cashing out £1,000 each week without anyone noticing.
Quite clearly, banks understand the imminent threat such events pose for their businesses. Yet they continue to happen – week in, week out.
What specific threats are considered “the norm” within the finance sector and how must banks respond if they are to have a secure future?
“In the past, the risk for thieves was often higher than the potential reward, but this has been turned on its head,” says Nigel Bolt, vice president and UK and Ireland country manager at Intel Security. The barrier to entry for cyber criminals is extremely low and, with the kind of cybercrime-as-a-service tools that can be used to rob a bank available online at low cost, almost anyone can try their hand at it.
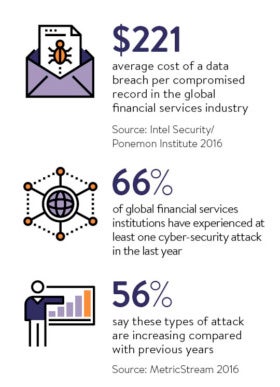
“Today a bank’s biggest asset is not just the money it holds,” Mr Bolt warns, “but the data of its customers.” And it’s this data that is often the target of the online attacker, which is hardly surprising given that bank and debit card data for “live” accounts, where no theft has yet been reported, can fetch more than £100 a pop within the criminal underworld.
There is big money to be made, with the Intel 2016 Data Protection Benchmark Study revealing there are between 21 and 30 data loss incidents every day across the UK financial services industry alone.
When it comes to threat specifics, phishing is at the top of the banking danger list. This insider threat is exploited by the phishing tactics of criminals and terrorists alike. Alicia Kearns, director at Global Influence, warns that increasingly cyber terrorism is taking the form of spear phishing attacks against banks and financial services.
These target specific individuals, often using social media accounts and postings to gather intelligence to use in gaining the confidence of the employee. The win? “Sensitive data and cash,” says Ms Kearns. “Despite the disparity between the size and structure of different banks, they all have one shared weakness – their employees.”
Andersen Cheng, chief executive of Post-Quantum, explains that often the immediate victims of phishing are not even the ultimate target, but instead form the easiest route into an organisation. Serious criminals will take weeks or even months to plan and execute their attacks, he says.
“It’s a fact of life that with greater digitalisation there also comes greater risk,” says Martin Day, managing director of corporate and professional qualifications at the London Institute of Banking and Finance. While the nature of the threat may change, Mr Day concludes: “We must ensure that those working in the banks are equipped with the professional skills to anticipate these risks and act accordingly with the highest of ethical standards in mind.”

Tesco Bank was forced to repay £2.5 million to 9,000 customers following the November hack
How banks are staying secure
But are our expectations of a secure bank unrealistic as we move forward into a cyber-banking dominated future? Rob Horton, a senior product manager at BAE Systems Applied Intelligence, doesn’t think so.
“We are in an arms race against the cyber criminals and fraudsters,” he says, “and the good guys are working day and night to maintain the upper hand.” Banks and industry partners are collaborating more than ever, securely sharing intelligence on the criminals who are seeking to attack the system. “This collaboration is increasing now on an unprecedented scale with the UK being a world leader,” says Mr Horton.
Nik Whitfield founded cyber-security software firm Panaseer after meeting cyber-security leaders at the UK’s biggest banks to get an insight into the key threats they face. “The question is not whether a bank is 100 per cent secure,” he cautions, “but whether a bank is secure enough.” This means defining a risk appetite at board level that depicts which bad scenarios a bank is likely to face and the frequency and loss they can accept.
Meanwhile Mr Cheng thinks that to succeed in building a secure bank requires rigorous application of several security technologies in parallel. What these technologies will be is open to some debate, although most forward-looking security experts include user authentication, non-repudiation and fraud deterrence along with the implementation of encryption that can survive in a post-quantum age. None of which can operate in a silo.
“The whole industry needs to be thinking about how they evolve to share intelligence,” Mr Bolt insists. “Banking security is not a competition point.”
What banks cannot do is allow the speed of change to catch them out. For example, today we can say that banking is largely a transactional experience where the customer is only recognised after they have logged in. As banking becomes fully mobile for more customers, then it will become about continuous validation and verification based on prior interactions.
“The bank will know who I am based on location, device, and most importantly the manner in which I bank and behave while on their systems,” says Paul Calatayud, chief technology officer at FireMon. “If I appear to be operationally out of the norm, I may be able to perform limited banking functions, while losing the right to perform more advanced functions until I am reverified.”
The whole industry needs to be thinking about how they evolve to share intelligence
What banks must do is become more agile when it comes to riding the security curve. The fight against cyber threats cannot remain asymmetric. Currently the norm for cyber-gang bosses is to plough 25 per cent of their profits from any heist straight back into research and development. If they want to invest more, they can make that decision on the fly.
“Criminals can adapt their techniques far more rapidly than the private sector’s budget and procurement cycles allow,” Mr Cheng warns. This is an area in which the financial sector is improving, but there is still some way to go in updating their process to enable the adoption of emerging solutions if the bank of the future is to look like anything resembling secure.


