Multifarious benefits of cloud computing make the disruption of digital transformation worthwhile, business leaders are assured. However, a recent torrent of automated attacks on cloud infrastructure’s vulnerabilities has precipitated a somewhat gloomy outlook, raining on the cloud’s silver lining.
In September, for example, Xbash – an advanced, data-destructive malware strain that combines cryptomining, ransomware and botnet capabilities – was identified. How can organisations that have come to depend on the cloud for the smooth running of their business combat these morphing, multi-vector cyberthreats?
“Cloud security has never been more critical,” warns Max Heinemeyer, director of threat hunting at Darktrace, a global leader in artificial intelligence-powered cybersecurity. “Xbash is a very sophisticated example of an automated attack because it can target both Linux and Windows servers, and has multiple payloads.
“Automated attacks against internet-facing infrastructure, like Xbash, are not new. What has changed is that the number of devices that are internet facing and potentially vulnerable has increased exponentially. This is in no small part due to the advent of the cloud. Attackers are innovating rapidly, and we can expect attacks on the cloud to get faster and more furious.”
Rise of the cloud has left vulnerable software exposed
 Charaka Goonatilake, chief technology officer of Panaseer, another cybersecurity giant, agrees. “What’s different in the cloud era is the ease with which exploitable software can be spun up and exposed to the world on the internet,” he says.
Charaka Goonatilake, chief technology officer of Panaseer, another cybersecurity giant, agrees. “What’s different in the cloud era is the ease with which exploitable software can be spun up and exposed to the world on the internet,” he says.
“Vulnerability search engines, such as Shodan, continually trawl the internet for these exploitable weaknesses and make it effortless to identify masses of targets to attack. Combined with the fact that highly sophisticated malware, such as Xbash, is readily available off the shelf, makes for a very low barrier for nefarious actors to carry out lucrative attacks from the comfort of their own homes.”
Hardik Modi, senior director of threat intelligence at Netscout, expands upon this worrying theme. “There are numerous instances of such open-source packages like Hadoop, Mongo and ElasticSearch which remain exposed to the internet, and there have been waves of reports of installations that have been exploited and encrypted,” he says. “This can have severe consequences for businesses of all sizes, since they may not be in a position to recover such data.
Indeed, our telemetry shows a Hadoop YARN installation is attacked about once a minute. A vulnerable installation would be attacked immediately. These measures vary wildly across the industry and as a result there remain huge exposures for the internet ecosystem at large.”
Rich datasets are valuable for both business and cybercriminals
Alarming figures illustrate the growing issue. “In January, 1.8 billion records were leaked online,” says Dr Guy Bunker, senior vice president of data security organisation Clearswift. “Today it is possible to collect and analyse billions of pieces of sensitive data in almost no time at all. It can be transferred across the internet to a partner who shares it with another and another, further enriching it with more data.
“These large datasets are not only useful for business, they are also a honeypot for cybercriminals who will steal it and then sell the information on the dark web. Security is only as strong as the weakest link.”
Adam Philpott, McAfee’s president, Europe, Middle East and Africa, points out C-suite ignorance. “We currently estimate that the average organisation generates over 3.2 billion events per month in the cloud, of which 3,217 are anomalous and 31.3 are actual threat events,” he says.
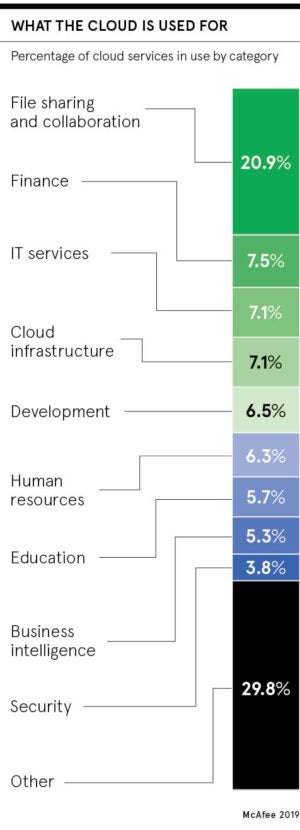
“Also, most organisations underestimate how many cloud services they actually use, with the average using approximately 1,935, a figure that has seen a 15 per cent growth from last year. In contrast, the average organisation thinks it uses just 30 cloud services.”
Improving cloud security is one of the biggest business challenges
Considering that the number of connected devices is expected to rise to 20 billion by next year, according to Gartner, organisations will use some 40 per cent of these and each one opens up a new vulnerability. Gartner also projects worldwide public cloud growth of 17 per cent this year. How then can organisations maintain adequate cybersecurity in this increasingly vicious online war zone?
Improving general cyber-hygiene and significantly greater education in this area, from top to bottom of an organisation’s hierarchy, is imperative. Adam Louca, chief technologist for security at IT infrastructure provider Softcat, says: “The current cybersecurity skills gap means defending cloud infrastructure from compromise is one of the biggest challenges of modern business.
“Cloud companies must do more to educate their customers on best-practice security configuration. Businesses must continue to invest in security skills training, and onboard new talent to close the widening gap between their security needs and the resources they have to protect themselves.”
Cloud security is not something businesses can afford to take lightly
Another level of protection is gained by using tech against tech, says Alan Duric, co-founder of Wire, an end-to-end encrypted communication and collaboration platform. “Automated attacks on cloud structures are directly related to businesses using insecure and unreliable communications platforms like email, Slack and WhatsApp,” he claims.
What has changed is that the number of devices that are internet facing and potentially vulnerable has increased exponentially
“Firms need to invest in secure communications platforms that are end-to-end encrypted, while ensuring all mobile devices used by the business are hardwired for security, and built with security and privacy from the ground up.” It’s clear that those who take a breezy attitude to cloud security risk being blown away in this stormy climate.
Rise of the cloud has left vulnerable software exposed

