Here’s a warning: “The world is still not prepared for cyberattacks on critical infrastructure. Governments are not ready, law enforcement isn’t ready, the facilities themselves are not ready, and the people who design, build and operate them are often the least ready of all. Unfortunately, the cybercriminals are very ready indeed.”
The difference between an attack on a single organisation and an attack on critical national infrastructure is there could be a real-world effect across an entire country
So says David Emm, principal security researcher at global cybersecurity provider Kaspersky Lab, who is not alone in his assessment of the current readiness among governments to protect critical infrastructure and the public institutions that exist under its umbrella.
While private sector operators take responsibility for their own digital safeguarding, such are the financial dangers associated with not doing so, Mr Emm asks: “Who will take responsibility for protecting our utilities, our rail lines or our healthcare system?”
Huge amount of public data held, without the IT security to defend it
 In the UK, the government holds information on individuals’ health records, residency, bank details and numerous other pieces of private data. By inadequately protecting such personal information against potential breaches, the ramifications could be disastrous.
In the UK, the government holds information on individuals’ health records, residency, bank details and numerous other pieces of private data. By inadequately protecting such personal information against potential breaches, the ramifications could be disastrous.
Mr Emm continues: “The difference between an attack on a single organisation and an attack on critical infrastructure is there could be a real-world effect across an entire country. In 2015, Ukraine had a taste of this, when hackers took control of its power grid, plunging thousands of homes and establishments into darkness for hours.”
Despite a growing awareness of the cyberthreat, many IT security models are still lagging behind, embedded in the hope that “security by obscurity” is enough. The challenge arises from the sheer volume of sensitive data that the public sector has to handle, against this entrenched slowness to adopt modern digital standards in the era of Industry 4.0.
Public sector security systems must become more robust
“Yes, data dumps of printed Excel files are still a thing,” says Alex de Carvalho, chief information officer and co-founder of PUBLIC, which helps tech startups solve prevalent public sector challenges and pitfalls.
“Many departments and local authorities have a pressing challenge to apply high standards of protection and oversight over a very disparate and digitally uneven network, and that’s where we have been working to try and find startups that can help public sector security teams tackle the cybersecurity challenge.”
Mr Emm and Mr de Carvalho agree that to implement reliable protection against all hazards, a multi-layered, highly configurable defence is required to extinguish more traditional threats, such as phishing emails, unsecure links and human error, and then dig deeper to ensure greater clarification of best-practice technology standards are in place for the companies or institutions themselves, their own internal arms, and their business partners and supply chain.
“Attacks on industrial systems are on the rise and it’s clear that for businesses operating industrial or critical infrastructure systems, the risks have never been greater,” says Mr Emm. “In 2017, TRITON, a malicious malware, took control of Triconex safety instrumented system controllers, giving attackers the ability to interfere with the plant’s processes or to cause an emergency shutdown, halting operations at a critical infrastructure organisation.”
Critical infrastructure and services, like the NHS, are under threat
Closer to home, it’s more evocative to resonate with the notion of a similar event happening within the NHS, a fact that hasn’t been lost on Barney Gilbert, co-founder and co-chief executive of Forward Health, a company offering secure messaging, compliant with the General Data Protection Regulation, for doctors and nurses as an alternative to open, prohibited portals such as WhatsApp.
“The NHS is a huge operation run by myriad staff, with varying levels of security clearance, most of whom engage with a unique combination of systems on a daily basis and the majority of which are processing highly personal data. It’s a minefield,” says Dr Gilbert.
“This hasn’t been helped by the piecemeal approach to IT upgrades that the NHS has spent several decades grappling with. It’s made for a set of weak systems that are perfect for low-cost, high-impact asymmetric cyberattacks or other security breaches, which could easily see our personal health data becoming a cyberwarfare bargaining chip.
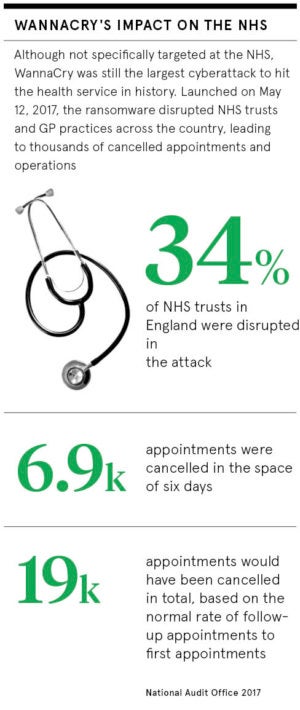
“We had a taste of what the impact of an NHS cyberattack looks like with the WannaCry incident in 2017. The impact was immediate and widespread, highlighting how vulnerable our most critical information systems can be.”

Last year’s WannaCry cyberattack showed just how vulnerable the NHS is to ransomware and other threats
Protecting critical infrastructure is tricky, but essential
Dr Gilbert says there shouldn’t be a difference in how critical network infrastructure or physical infrastructure is protected, adding that governments need to make systems too “costly and ultimately counter-productive” to be attacked.
Mr Emm says: “Fast-changing threats have made it impossible to secure critical national infrastructure networks and systems completely, but a wait-and-see attitude should not be adopted. In fact, it should serve as the latest warning that hackers can severely affect, or even take offline, critical public infrastructure.
“Updating plans for improving defences and reducing the impact of attacks must become the new normal if the government and operators are to be agile in responding to this changing environment.”
There is an overwhelming consensus that a reactionary approach to the current situation is not enough. To get ahead of the curve, a mixture of holistic system protection, on the surface, and improved networking, education and training, behind the scenes, is vital.
“Essentially, every industrial customer and process is unique, and it is important to deploy a solution made up of a portfolio of technologies and services that can adapt to different sectors, whether that’s oil and gas, water, power grids, manufacturing and so on,” says Mr Emm.
Mr de Carvalho believes inroads are being made in the UK through not just workshops and classes, but physical tools that are able to “quickly and effectively notify individuals and management of potentially unsecure actions”.
By following a comprehensive, process-oriented approach, critical network infrastructure will be better guarded against sophisticated, targeted attacks, veering away from an inefficient, reactionary seek-and-destroy approach to an embedded culture of front-line public protection.
Huge amount of public data held, without the IT security to defend it

