There was a time when a fraudster who had acquired your cashpoint card and discovered your PIN number could steal a few hundred pounds from your bank account through a cash machine. Today the threat is much more serious. Cyber criminals can steal a customer’s bank details and not only help themselves to that person’s entire funds and assets, but they can gain access to almost every aspect of their lives. These criminals are increasingly more enterprising, more ambitious and better resourced.
Around two years ago, researchers at Kaspersky Lab made a disturbing prediction. They foresaw financially motivated cyber fraudsters adopting the sophisticated techniques previously identified with groups of hackers responsible for what is known as an advanced persistent threat (APT), in other words the continuous, long-term hacking of an organisation, often for political reasons.
The prediction came true just a few months later when Kaspersky Lab announced that it had identified a cyber-crime gang called Carbanak that was using custom malware and APT techniques to steal what could be as much as $1 billion from up to 100 financial institutions in at least 30 countries.
Since then the company has seen an increase in these covert, APT-style attacks that combine the use of reconnaissance, social engineering, specialised malware and long-term persistence to steal money from financial institutions, particularly cashpoints and money-transfer systems.
Alongside this trend is another worrying development, according to Kirill Slavin, UK and Ireland general manager at Kaspersky Lab. “We’re also seeing cyber criminals increasingly working in collaboration with traditional fraudsters in a blend of online and offline fraud,” he says. “These old-school crooks collaborate with internet criminals to hack online systems, and hijack video cameras and keyboards, so they can see exactly what bank employees are doing. They then share their detailed knowledge of how banks work.
“In some cases, for instance, they will invent a company with fake employees who are receiving fake salaries, but this is still real money that’s being paid out. They have knowledge of the online world and they use this to help them to do things that criminals have been doing for years.”
Traditional and cyber-crime gangs are merging and, along with the perpetrators of APTs, they’re finding more weak points in financial institutions. For banks and building societies, the risks are both financial and reputational as they’re forced to compensate customers and apologise to them, as well as often dealing with adverse media coverage.
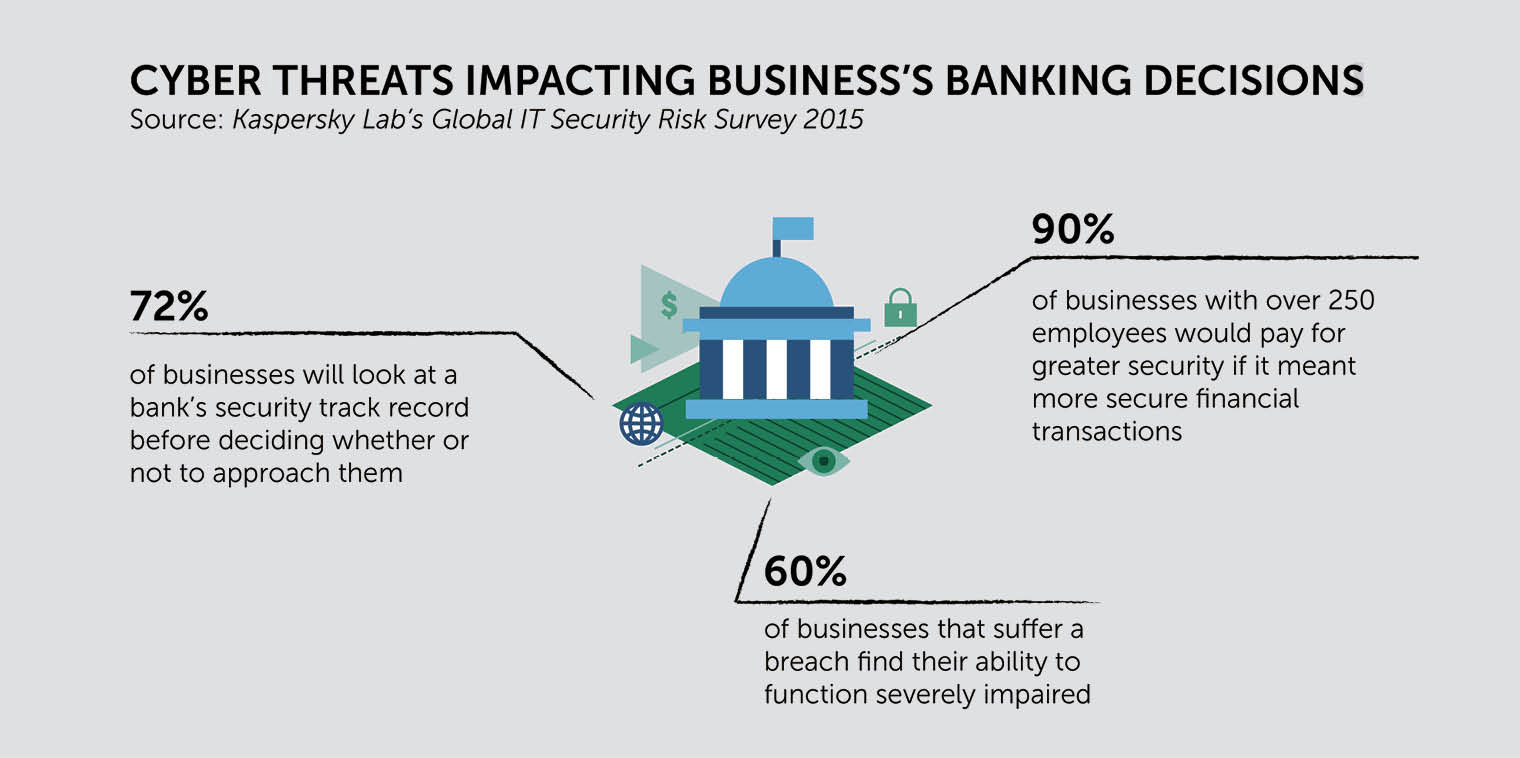
The good news is that financial institutions don’t have to choose between ease of use and security – they can have the best of both worlds
“The banks face a dilemma,” says Mr Slavin. “They want to make customers’ lives easy and to ensure that all transactions are smooth, swift and seamless, but they also need to ensure that they’re secure. Making things easy for customers, so that they’re more likely to remain loyal was why, for instance, banks in the US were reluctant to introduce the chip-and-PIN system. They’re now having to bring it in though.”
However, card readers and other, similar technology not only slow the transaction process, but often lead to a false sense of security as they’re not always as effective against fraud as many people assume.
As attacks become more frequent and sophisticated, some banks are increasingly taking the view that they’d prefer to quietly and discreetly compensate customers for any loss than introduce more cumbersome security. “The problem is that this approach is a bit like paying kidnappers,” says Mr Slavin. “The more you do it, the more you encourage fraudsters to attack you as they realise that you’re willing to tolerate higher levels of fraud.”
The good news, he reveals, is that financial institutions don’t have to choose between ease of use and security – they can have the best of both worlds.
“Until recently there has always been a big divide between business-to-business or corporate security on the one hand and customer security on the other,” explains Mr Slavin. “In effect, the banks have their security and customers have their own. But a few years ago, Barclays started to buy consumer security products from us in bulk and give them away to their customers.
“At the moment this is only entry level, but we’ve suggested they also look at something a little bit more substantial. Customers would have to pay for this, but they’d receive a big discount, typically around half the normal price of the product.”
But it’s the second phase of this initiative, which began around a year ago, that is particularly exciting and offers great benefits for the financial services sector as a whole. Working with another bank that cannot yet be named, Kaspersky Lab’s technology can now report back to the bank when a customer’s device is subject to an attack. This means the bank will be able to identify how much risk that customer is subject to.
“Meanwhile, we also provide the bank with threat intelligence feeds. These present a real-time picture of the world – which attacks are happening where and when as they happen, as well as which are successful and which are not,” says Mr Slavin.
“The bank can then compare this information with the data that it’s receiving from individual customer’s devices. This allows it to understand not only which consumers are affected, but also what kind of attack they’re being subjected to. The banks can then act to reduce the risk they face from cyber criminals and the traditional fraudsters they work alongside. Banks have hitherto not thought of putting these two elements together.”
Over the next few years, more and more banks will introduce high-tech security features such as biometrics, including voice, face and iris recognition. First Direct, for instance, recently launched a voice-recognition system for its customers. However, in a traditionally conservative sector where no one institution wants to be seen as pushing the boundaries too far too quickly, caution is the watchword.
“These new technologies will arrive at some point down the line,” predicts Mr Slavin. “But in the meanwhile, banks can connect their customer and corporate security to each other to allow information about attacks and threats to be sent from devices to the bank’s corporate security centre. This merely requires adding a few words to the customer’s terms and conditions. Banks don’t even have to reorganise their security departments. Taking this approach represents a paradigm shift in the way they handle security.”
For more information please visit www.kaspersky.co.uk
