In 2010, Daniel Houghton, a former employee of MI6, was convicted of disclosing electronic files to Dutch security services. This was a classic insider threat, where a trusted member of staff with a grudge represents a clear and present danger to public sector organisations. When this person has detailed knowledge of IT systems or, perhaps, is even a member of the IT team, the results can be spectacular.
But really, it’s not the person that IT security teams need to concentrate on. Preventing them causing a catastrophe is less about the person and more about the method used to access sensitive data within the local council, hospital or government department. Privileged access, not people, is the true insider threat. Securing privileged accounts should be ongoing with continuous evaluation and adjustments to improve security as the threat landscape changes.
Why is it not about the person? At some point, you’ve probably thought about what you would do if you were invisible for the day or where you’d go if you could time travel. In the digital age, the equivalent might be to ask yourself what you would get up to if you had advanced cyber skills. Would you spy on or compromise your employer if you could?
The basic rule in defending against malicious insiders is to address the threat, not the individual
Every UK worker knows that you can’t just access any data you want to get your hands on. Confidential files are locked away from the eager eyes of curious staff. Access to information is limited, whether it is private e-mails between colleagues, your team members’ salaries, performance reviews or data on UK citizens. But, if you were given the opportunity, what systems or data would you want to access? What would be the most coveted information?
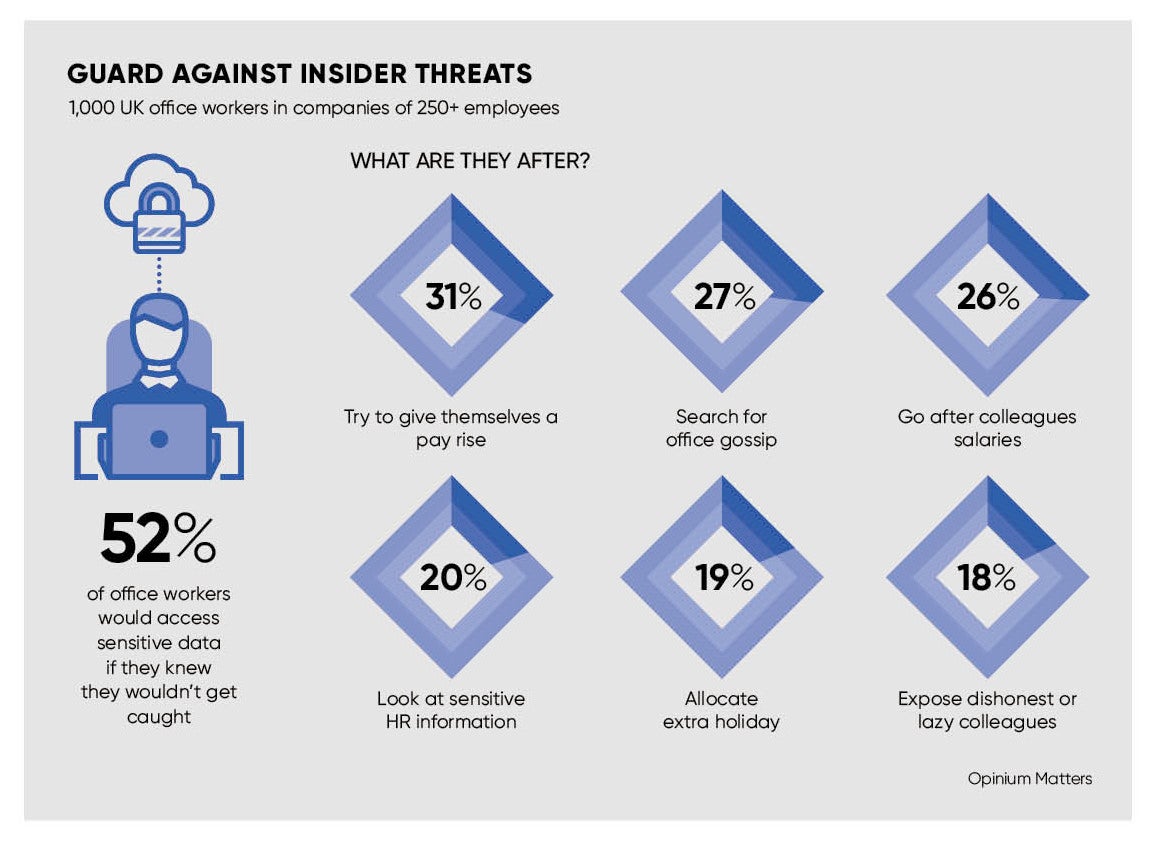
CyberArk’s recent poll of 1,000 UK office workers revealed that even the happiest staff would be tempted to access sensitive information if they knew they wouldn’t get caught. In fact, more than half (52 per cent) of workers surveyed would browse off-limits data.
Spying on public sector data is one thing, but cyber criminals are increasingly going one step further, actually altering information on servers and databases. Given the opportunity, every day UK office workers would follow in hackers’ footsteps and alter information on their organisation’s system if there would be no repercussions for themselves.
The motives for this primarily revolved around time and money, with almost a third (31 per cent) wanting to treat themselves to a pay rise and one in five (19 per cent) allocating extra holiday to themselves.
The immorality of the act is not a problem for more than one in five (21 per cent) staff, who say it is their technical ability, not conscience, holding them back.
With the average person’s cyber skills improving all the time, the UK public sector must be more aware than ever of the insider threat. This includes having systems in place to monitor and stop unwanted insiders in their tracks to protect their most valuable information.
So, what can the UK public sector do to stay in control? Take a close look at IT. The number of high-value application and admin accounts that businesses have on their network is often hugely underestimated. Every single one of these needs to be closely managed and secured to ensure they don’t become a point of vulnerability.
Basic controls are still essential, including creating one-time passwords, automatically changing them on a 30 or 60-day cycle, and putting controls to ensure passwords are as complex as possible.
The basic rule in defending against malicious insiders is to address the threat, not the individual. Give the right users the right access at the right time and keep confidential information locked down.