What impact did lockdown have on companies’ exposure to cyber-threats?
Organisations had to rapidly adopt new systems, processes and procedures to accommodate remote working, and aggressively roll out existing solutions not widely used pre-lockdown. With everybody suddenly operating from home, patterns of work, and therefore network usage, changed too. The attack vectors changed, as did the points of weakness in organisations’ information security. All this had a major impact on risk and management of cyber-threats. The sheer speed at which organisations had to adapt meant many did not have the time to do their standard diligence on providers and suppliers, which led to the deployment of solutions based on incomplete information and the possibility of latent security flaws. If these issues are not picked up quickly and acted upon, organisations are susceptible to problems down the line and greater exposure to cyber-threats.
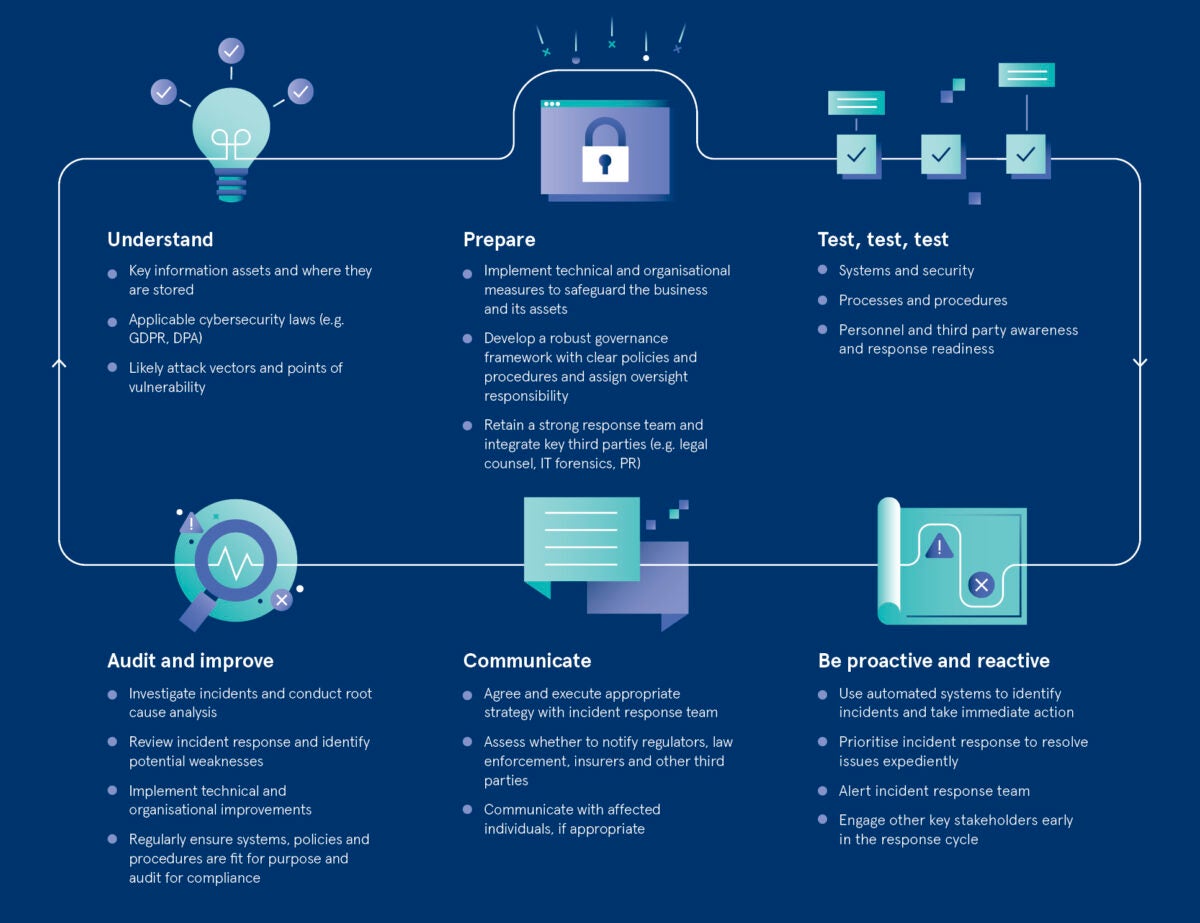
If a major incident does occur, what are the immediate steps an organisation should take to respond?
It’s something every executive fears: that call in the middle of the night saying that there has been a major cyber-incident. The speed of response is vital; as much information as possible must be gathered in those very early moments to understand what information and systems have been compromised. Has this happened before and does it indicate a systemic issue? What is the risk to the organisation, its reputation and its customers? Establishing that initial snapshot assessment is incredibly important as it will drive not only the prioritisation of the response, but the entire process. If an incident is correctly identified as high risk at the onset, the response timeline will accelerate, with organisational resources deployed more appropriately.
Once that initial risk assessment is complete, what should happen next?
Principally, it’s about damage limitation and controlling the incident, so understanding the mitigating factors that might help to reduce risk to the business is key. If information has been lost or stolen, for example, was that information subject to encryption? Is it in a format that would be useless to a third party? Did the incident involve theft of a device that has since been recovered? If, following that risk assessment, you conclude that it is a major, high-risk incident, then the response must be fast. It may be necessary to first internally escalate by notifying the executive committee or wider board. External legal counsel should be involved as early as possible so they are on call to respond whenever needed throughout the incident. Engaging legal counsel has the added benefit of establishing privilege in certain circumstances, which can protect sensitive discussions from future disclosure should there be an investigation or litigation. Forensic IT experts are also an essential part of the damage limitation process, particularly in identifying the threat, understanding what went wrong and taking the appropriate measures to stem the tide. Regulators need to be informed as soon as possible, as should affected individuals, where organisations are legally required to do so.
What elements of response are sometimes overlooked?
Public relations plays an often overlooked, but absolutely crucial, role in controlling the narrative and allowing the organisation to present the best and most accurate representation of the incident. At each stage of the response process, it is also vital to preserve evidence and record details of every action and decision that was made. You may look back and determine that, in hindsight, poor decisions were made, but if you can show precisely what information guided those decisions at the time, it can be beneficial in the event of an investigation or litigation. Of course, excessive retention of records and information can also present challenges, but legal counsel will be able to assist in striking the right balance.
How does White & Case support companies in this important area?
Cybersecurity incidents do not respect national borders. Companies are often affected in multiple jurisdictions, with different regulators and laws in relation to disclosure obligations and timeframes. White & Case’s global Cyber Incident Response team has extensive experience working with clients that have a multi-jurisdictional footprint. While we work with these clients through all stages of the preparedness, response and review process, we are uniquely positioned to assist during the critical incident response phase. This is due to our global presence and cross-disciplinary team of cyber-experts who are constantly collaborating with each other and with PR, IT forensics, internal compliance and incident response teams, helping to deliver crisis management and legal advice whenever and wherever it is needed.
For more information please visit whitecase.com/cybersecurity
What impact did lockdown have on companies’ exposure to cyber-threats?

