The traditional concept of a network security architecture, where teams build secure perimeters around corporate assets and police the traffic that comes in and out, still underpins the security strategy of many organisations. But in the era of cloud, it is no longer fit for purpose.
The growing patchwork of vendors required in a perimeter-based security approach is a source of daily frustration for chief information security officers (CISOs). In a study by Netskope in early 2021, 46% of global IT leaders said they are looking for an opportunity to consolidate network security vendors. This is one of the reasons that, in 2019, Gartner recommended a new approach to security architecture, Secure Access Service Edge (SASE). A software-defined, cloud-delivered architecture, SASE protects anywhere-anytime access to digital services.
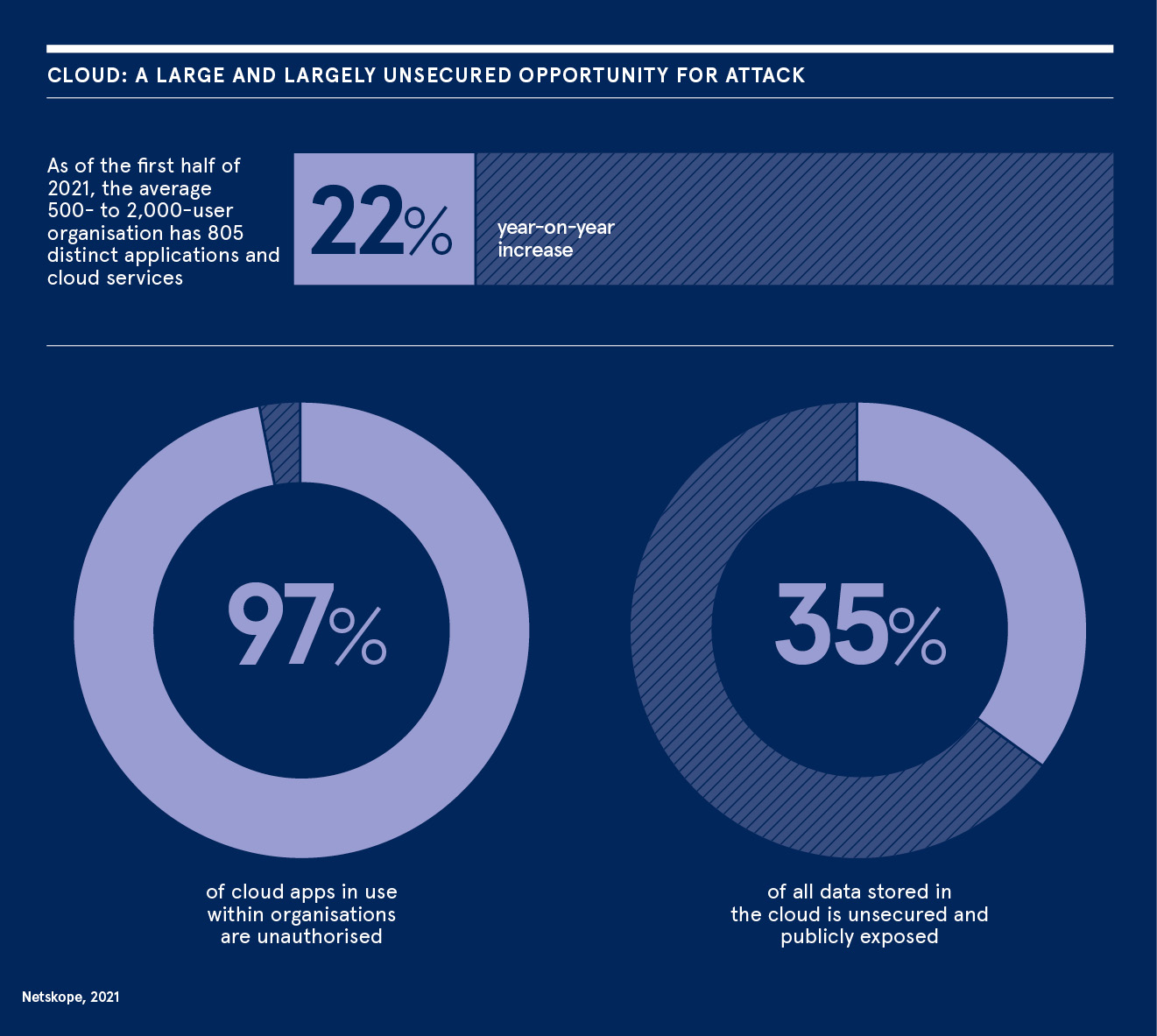
Just months after Gartner presented the SASE approach, the arrival of the Covid-19 pandemic vastly accelerated its urgency, as organisations rapidly adopted remote working to survive. With employees having now spent 18 months juggling work, school and life across a mixture of corporate and personal devices, the reliance on cloud applications has exploded. As of the first half of 2021, the average 500-2,000 user organisation has 805 distinct applications and cloud services, a 22% year-on-year increase, according to Netskope.

Every company has become a cloud organisation during the pandemic, and research firm 650 Group forecasts the SASE market to grow by 500% between 2020 and 2025. As teams moved swiftly to select and authorise cloud services as the only way to onboard and upscale essential services, ‘shadow IT’ use among remote workers spiralled. Unauthorised cloud apps in use within organisations is as high as 97%, Netskope’s data reveals.
“The impetus for change was already there, but nobody realised what was just around the corner in the form of a global pandemic that further accelerated the need for SASE,” says Neil Thacker, chief information security officer EMEA at Netskope, a market leader in SASE.
“We’re seeing a lot of requests from organisations to consolidate. They’ve realised they have too many overlapping legacy network and security controls and instead want to leverage approaches such as zero-trust network access but don’t want multiple disparate products to do it. They aren’t too concerned around how they connect to key services and data, they just want to connect securely, without any degradation in performance, and to use the same security policies across all traffic and data flows.”
Cyber threats, meanwhile, are adapting quickly to this new landscape. More than two-thirds of malware is now delivered via the cloud, predominantly through cloud storage apps. Cybercriminals use the same cloud services in their attack as the enterprises they target, so the URLs that host the nefarious payload are familiar and trusted by their targets. Phishing attacks are also still common, and they are increasingly linking back to a cloud service as threat actors themselves are outsourcing their architecture to help bypass an organisation’s security controls.
“There has been an increase in both the prevalence and sophistication of threats,” Thacker adds. “Most notably, threat actors not only use cloud services to deliver their malware and payloads but they also target cloud infrastructure and applications looking for misconfigurations. There are now thousands of cloud services and security teams are often asked by the business to enable direct access to them. Of course, when you put in a bypass or allow this type of connectivity without any security controls, threat actors will be ready to actively exploit these gaps.”
Organisations that are no longer able to put walls up around their data in private data centres are more at risk of user error when applying security settings to cloud-stored data, leaving over 35% of all data stored in the cloud exposed. By following the data, a SASE approach can spot these security gaps and either automate a remediation, or coach employees when inappropriate high-risk behaviours are identified, making the security team’s role less reactionary and more proactive.
Traditional security products interpret the language of HTTP(S) and so fail to spot issues in trusted cloud services. SASE can do this, but it also interprets the languages of cloud, such as API, and so is able to provide the granular inspection of data needed to protect against cyber risks and threats. After using Netskope to analyse its data traffic, one large manufacturing firm discovered that the organisation had over 800 unique instances of Google Drive. One was the corporate instance, while the rest were personal and third party instances. The only way to accurately identify them was through API decoding.
Large architectural IT redesigns may often come with big price tags, but early SASE adopters are reporting the opposite. As SASE is in the cloud, it is operational rather than capital expenditure, and by replacing traditional appliances it has helped eradicate the need for painful and expensive hairpinning of traffic flows. Crucially, early adopters are reporting cost savings of millions of pounds from removing Secure Web Gateways, VPN and WAN hardware, as well as MPLS bandwidth savings.
“Organisations are realising cost savings from 15% to 30% by moving away from hardware and adopting a SASE architecture,” says Thacker. “But a key benefit, beyond cost and consolidation, is visibility. As enterprises move more and more data to cloud services, these services are becoming the default target. We are also seeing an incredible number of unauthorised or unmanaged cloud applications being used, and all the while there are ongoing challenges around data sovereignty and compliance with data protection laws.
“We urgently need to fix the visibility gap because 97% of cloud services being unauthorised and unmanaged is way too high. Organisations must bring that down to a more manageable level. The CIOs and CISOs we interact with see the need for better visibility of what cloud services are being used as their number one priority. If they don’t know what is being used, how can they apply an appropriate form of security control? SASE identifies what cloud services are being used; by whom, for what purpose, exactly what data is going there, and where it is located.”
For more information about the latest cloud security threats, download Netskope’s most recent Cloud and Threat Report at: https://www.netskope.com/netskope-threat-labs/cloud-threat-report
Sponsored by

