The 5G era is about to arrive, bringing faster speeds and lower latency to enable a host of new business applications. The next-generation cellular technology is designed to be more robust than its predecessors 3G and 4G, but 5G security is also much more complicated to manage.
5G poses an elevated security threat partly because there are more vectors through which adversaries can attack. The technology is set to enable a huge number of connected devices, collectively known as the internet of things (IoT).
Yet IoT devices are a target for cyberthreat actors because they could be taken over to form what’s known as a botnet to perform distributed denial of service, or DDoS, attacks to paralyse networks.
The challenge is amplified by vertical 5G use-cases, such as connected cars and healthcare, which bring critical industry-specific security requirements. At the same time, 5G is based on virtualised networks which themselves need to be governed by robust protocols.
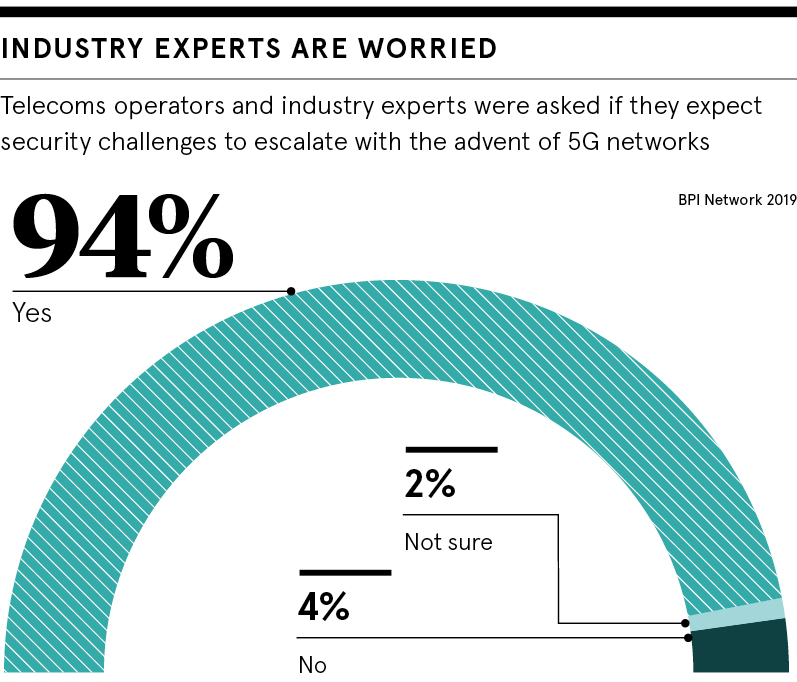
The real-life risks posed by 5G are already being demonstrated. Last year, researchers at the Black Hat security conference shared 5G vulnerabilities that allowed them to access user locations and launch attacks on devices.
Later in 2019, researchers at the US universities of Iowa and Purdue demonstrated 11 5G vulnerabilities that could allow denial of service attacks and hijacking of the public paging channel used to broadcast emergency alerts.
5G security creates an urgent need for the ecosystem – mobile operators, physical infrastructure providers, such as Nokia, Ericsson and Huawei, vertical industries, such as automotive, and regulators – to work together. So how can this be done?
5G security threats
Firstly, the 5G security challenges need to be acknowledged and addressed. Some of the greater threats are posed by high-risk industries using 5G technology for mission-critical applications. For example, 5G will enable smart cities and self-driving cars. Specifically, this will see 5G networks underpinning services such as emergency response and traffic control.
But if the 5G networks enabling these applications are interfered with or shut off, the results could be catastrophic. “What happens if a hacker shuts off a city’s water supply or if they are able to gain access to an army of delivery drones?” asks Russ Mohr, engineering director at MobileIron.
Due to the network architecture, 5G will also see the impact of failure of the core infrastructure increased. “Current core infrastructure has isolated functionality so when a component fails, such as mobile data or SMS, it results in a partial degradation of service for a single network,” says Alex Farrant, senior researcher at Context Information Security. “5G’s shared infrastructure has the potential for mass failure across multiple networks.”
Switching between networks increases risk
Another security risk is posed by the protocol designed to allow 4G or 3G connections when a dependable 5G signal isn’t available. When a 5G device switches to 3G or 4G, it’s exposed to the vulnerabilities that haven’t been addressed in the previous generations’ protocol.
When switching from 5G to 3G or 4G, the architecture will rely on seamless handover between those two networks, says Nick McQuire, vice president of enterprise research at CCS Insight. “How can the mobile network operator guarantee there isn’t weakness in the handover?” he asks.
The 5G supply chain is a further challenge. Recent concern has centred on the potential threat from network infrastructure provider Huawei, which has just been given the go-ahead by the UK to be deployed in less critical parts of the national 5G network.
But many fear the manufacturer will engineer a “backdoor” allowing it to snoop on data. With this and other 5G security threats in mind, the European Commission issued a 5G toolbox to help European countries co-ordinate their approach.
Standards bodies, such as the 3GPP ETSI and the IETF, are also working on 5G standards and specifications to secure the standalone version of the technology set to enable business applications.
5G: more secure than 3G and 4G?
As the threat landscape widens, 5G security is certainly a complex task. But if the ecosystem addresses the issues, the technology will be more secure due to better encryption than 3G and 4G, says Daniel Valle, chief technologist at World Wide Technology. “Each evolution is more secure than its predecessor and that doesn’t change with 5G,” he says.
At the same time, while things are at an early stage, 5G’s architecture allows mobile operators to offer security insights to businesses. “The operator can provide visibility of traffic going across the network, so companies can see anomalies or if someone is trying to intercept it,” says McQuire.
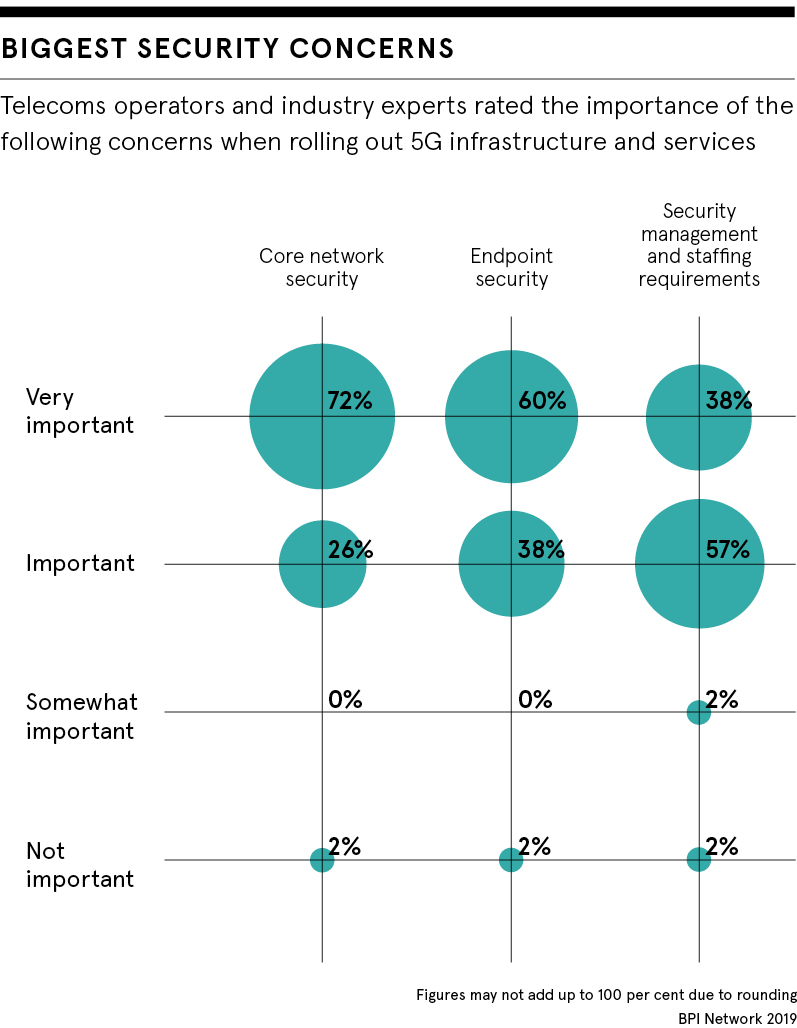
Meanwhile, network slicing, which allows mobile operators to effectively slice the network into different use-cases or requirements, could add security capabilities for 5G. McQuire says slicing can add security because it is “almost your own private channel”.
“If there’s an attack on the public network, for example Vodafone’s network goes down, the sliced environment would, in theory, be immune,” he says.
Work is being done to secure 5G, but who is responsible for this? “In the early phases, a lot of responsibility has to fall on the service and vendor ecosystem,” says McQuire. “Operators will sell 5G services to enterprises. The emphasis will be on network and infrastructure providers to be on the same page, looking at the benefits and risks.”
Is 5G security a shared responsibility?
In many ways 5G is a “shared responsibility model”, much like cloud services, says Cradlepoint chief security officer Todd Kelly. He says: “Standards bodies dictate how to implement a secure 5G network architecture and operators are responsible for the security of the network.”
Enterprises are responsible for data being transported across networks. “But mobile network operators must embrace a continual risk-based approach to monitoring their network and services, evolving their security controls around emerging threats,” Kelly adds.
Mark Hawkins, fellow and 5G lead at QinetiQ, says it’s important these groups are “aligned and collaborating to ensure end-to-end security”.
In the meantime, businesses need to be aware of 5G security problems and risks so they can prepare for its arrival. It’s true that 5G will offer huge benefits, but one thing is certain: the technology will require much more focus on security. As McQuire concludes: “If it’s going to realise its vision, 5G security needs a lot more attention.”
