Cybercriminals have done their best to disrupt national elections around the world over the last few years, be it through fake news campaigns or by directly hacking officials’ e-mails.
But none has got as far as breaching a country’s online voting systems and manipulating a result – at least, not yet.
It was alarming, then, when in July a team of ethical hackers at the Def Con cybersecurity conference unmasked a raft of vulnerabilities in US e-voting machines that would let a criminal do just that.
During a session at the Las Vegas event, the security experts managed to hack into and take control of 30 commonly used voting terminals, sometimes in a matter of minutes.
Many of the machines were found to be running insecure software or to have exploitable loopholes in their hardware. Others, such as the WinVote machine, used in local elections in the US state of Virginia in 2015, had flimsy security settings.
Hackers were able to hijack the unit via its wi-fi connection and once inside discovered it was secured with the password ABCDE.
In reality, the chances of state-sponsored cybercriminals hacking into voting machines during an election are still remote, says Lance James, chief scientist at the cybersecurity firm Flashpoint.
That’s because terminals in America are not connected directly to main servers, so a hack is only really possible at close range, as happened at Def Con.
However, that hasn’t stopped state-sponsored hackers trying in the past, raising the prospect of more sophisticated attempts in the future.
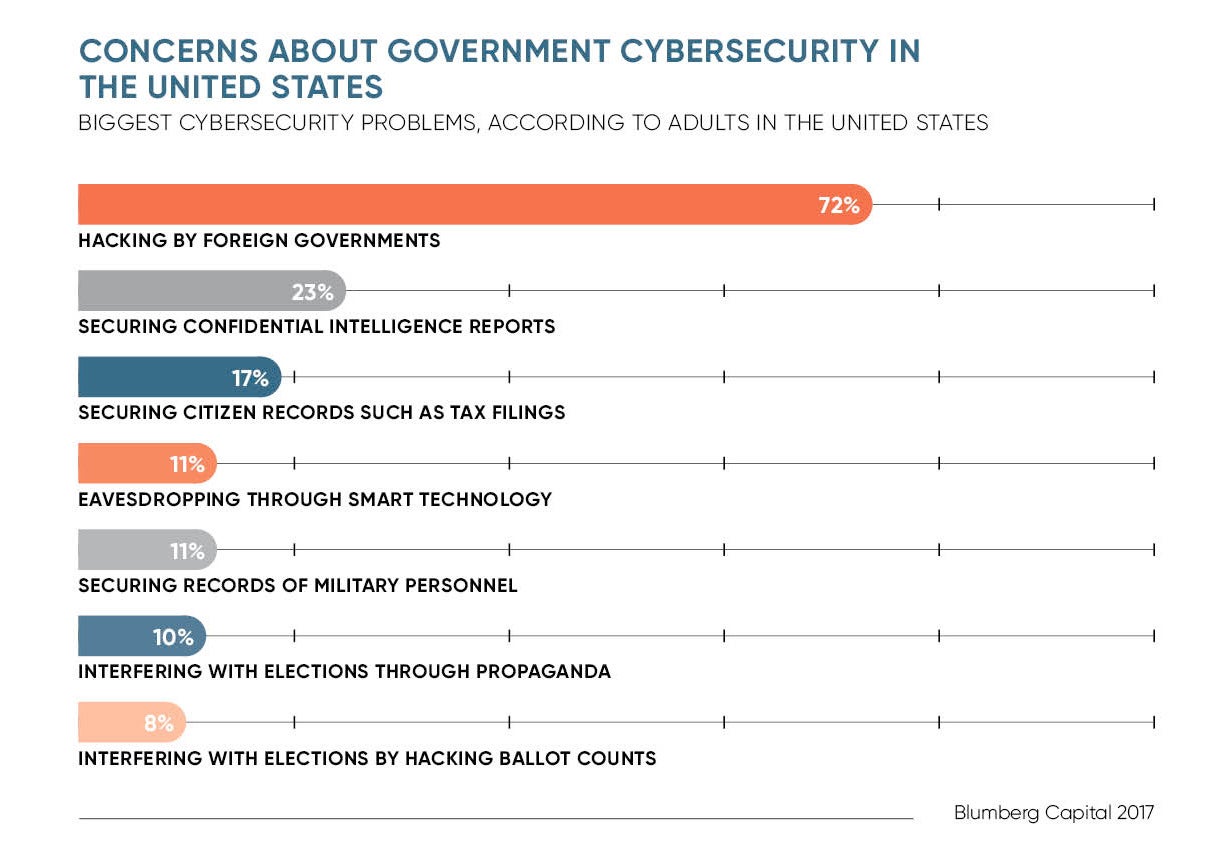
In September, the US government revealed that the electoral systems of 21 states had been targeted by Russian hackers before last year’s US presidential election, including in key political battlegrounds such as Florida, Ohio and Pennsylvania. These attacks led to some personal information being exposed and two voter registration systems being temporarily shut down.
“When it comes to the ability to remotely modify a vote over the internet, then the majority of systems are designed to deal with that threat model,” explains Mr James.
“But that doesn’t mean to say that a voting system can’t be hacked, only that it would likely require a combination of opportunity plus mission-oriented planning to successfully pull off such a hack without detection.”
Some argue that the mere threat of such an attack may be enough to undermine trust in democratic institutions anyway, which is exactly what cybercriminals targeting elections want.
In a survey of 5,000 voters, published earlier this year, cybersecurity firm Carbon Black found that one in four US voters were considering not voting in upcoming elections due to concerns such as theft of personal data from election databases. That’s a 7 per cent rise over a similar poll conducted in September 2016.
Moreover, in September, the Kenyan Supreme Court was forced to annul the country’s August general election result following allegations of online vote rigging made by a vanquished opposition party.
There are cheaper and easier ways for a foreign state to sway the result of an election than attacking its voting systems, says Arun Vishwanath, an expert in cybersecurity, at the University of Buffalo.
All it takes is a simple phishing e-mail targeted at an unsuspecting or busy individual
One would be to deploy disinformation, for example a fake news campaign on social media. Another would be to hack the e-mails of officials involved in the election process itself, via phishing or malware attacks.
“That way you can orchestrate leaks and cast seeds of doubt about the integrity of the electoral process,” he says.
Hacks of officials from the Democratic National Committee (DNC) and the Hillary Clinton campaign wreaked some of the greatest damage in last year’s US presidential election campaign, with the pilfered communications later appearing on whistleblowing site WikiLeaks.
According to Matt Lock, of data protection firm Varonis, political parties are particularly vulnerable to cyberattacks because they store masses of sensitive data across multiple devices, including communication strategies, membership information, donor details and financial data.
“All it takes is a simple phishing e-mail targeted at an unsuspecting or busy individual, or an unassuming USB stick connected to any campaign-related device, and a hacker has access to everything on the system, particularly if the system has ‘open access’ settings in place,” he says.
Modern democracies clearly have a battle on their hands to protect the integrity of their elections and many are now pursuing defence strategies.
In the United States, both the Democrat and the Republican parties have been making significant investments in improving their cybersecurity, with the DNC having hired former Uber executive Raffi Krikorian to lead its IT operations.
Mr Krikorian has already instigated reforms including directing all DNC staff to use the secure messaging app Signal instead of text messages, implementing simulated phishing drills to prepare employees for cyberattacks and introducing the use of two-factor authentication to log into DNC systems.
The UK, whose parliamentarians were the subject of an Iranian-linked hack back in June, is also taking precautions.
Government agency the National Cybersecurity Centre says the country’s voting systems themselves are not at risk of attack because they are paper based.
But it has been providing advice and guidance to political parties, local authorities and the Electoral Commission, equipping them to protect against a wide variety of threats including DDoS (distributed denial of service) attacks, spear-phishing, fake e-mails and malware.
According to Dr Vishwanath, democracies will continue to fight an “asymmetric battle” in which hackers are spending small amounts of money to cause havoc, and it is highly unlikely we will stamp out hacking and propaganda campaigns altogether.
That said he believes greater awareness of the risks is helping countries to bolster their defences.
Take Germany, which largely avoided cybermeddling in its federal elections in September because it was well prepared. Among other measures, its major political parties entered into a gentleman’s agreement not to exploit any information that might be leaked as a result of a cyberattack.
Officials also sought to weed out vulnerabilities in parliamentary and election authorities’ IT systems, and major news media outlets set up teams of fact checkers to protect against fake news.
“The Germans started talking about the risks of Russian attacks from the get-go and publicised hacking attempts as soon as they saw evidence of them,” says Dr Vishwanath. “They learnt the lessons from the French and the US elections, and I think it made a difference.”