
The ‘dark web’ isn’t only the home of illicit marketplaces for drugs and weapons, although those can certainly be found. It is also becoming a crucial recruitment platform for gangs of cybercriminals.
As the infrastructure behind ransomware-as-a-service becomes ever-more professional and sophisticated, the dark web – unlisted websites only accessible via encrypted technologies like the Tor network – is an important space to understand how cyber attackers tick. For businesses, it can offer valuable insight into how criminal gangs are targeting white-collar IT professionals and why they are succeeding.
What is the dark web and who uses it?
There’s much mystification about the so-called dark web. Its moniker brings to mind 90s hacker aesthetics and Mr Robot-style cyberpunk worlds. But really the dark web just refers to a private, usually encrypted network that’s not visible on the public internet most of us use every day. Typically this requires some know-how, such how to connect to and navigate the Tor network, in order to access it.
Despite its ominous-sounding name and shady reputation, not all dark-web dealings are nefarious. “There are a huge number of people who are active there for perfectly legitimate reasons,” says Mark Frankel, who teaches a course on the dark web for The London Interdisciplinary School. For example, users might be political dissidents in countries that face repression or they may have the need to circumvent online censorship.
Others’ needs may be more prosaic. Some users might recently have been evicted with no fixed address, so are unable to procure medication via the usual legal channels. Others might need to protect their anonymity for a whole host of reasons, Frankel adds: “Dark web users might be people who have had a previous run-in with the authorities. They are perfectly legitimate but still prefer to operate in a more clandestine environment.” Many simply don’t wish to be tracked on the public web, as the rest of us are every single day.
How cybercriminals are using the dark web
But there are those who take to the dark web for criminal purposes. Perhaps most notorious are the dark web marketplaces, such as the now-shuttered Silk Road and Hydra Market, where users could freely trade in illegal goods.
One increasingly lucrative revenue stream among the drugs, weapons and counterfeit goods is cybercrime. Dark web markets, even following international crackdowns by law enforcement, were worth $1.7bn (£1.3bn) in 2023. Given that most individual ransomware payments totalled in excess of $1m (£760,000), it’s reasonable to assume cybercrime constitutes a fairly sizeable chunk of dark web market value.
On these marketplaces, users can pay for attacks ‘as-a-service’ – where the technical expertise to conduct the attack is farmed out. Buyers can pay for criminals to deploy ransomware or Distributed Denial-of-Service (DDoS) attacks or to target individuals for their passwords or for other fraudulent reasons.
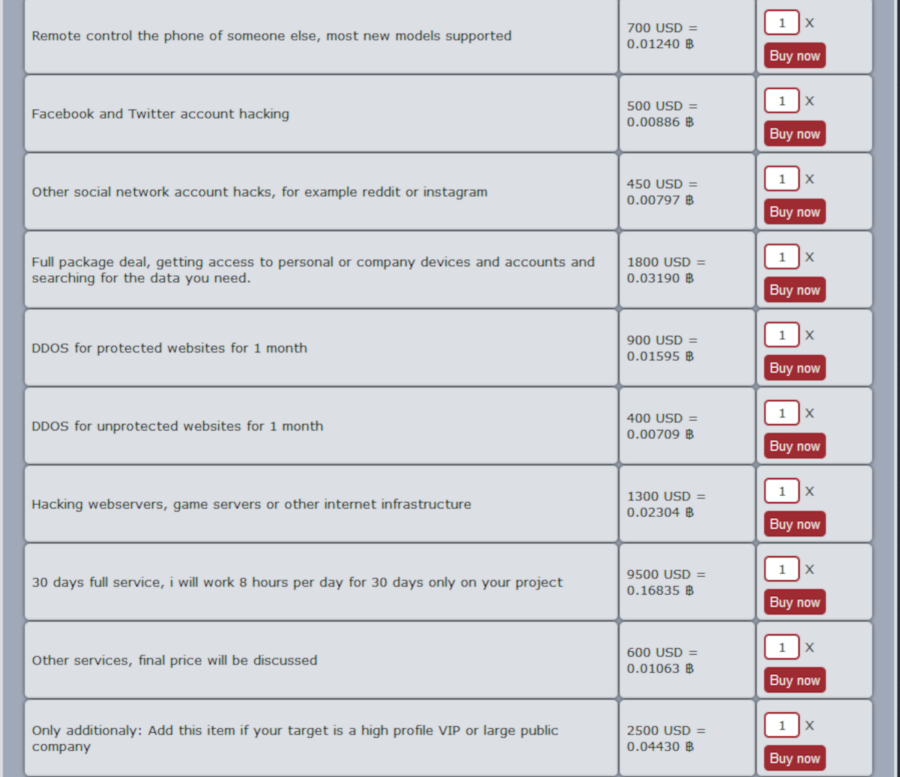
Services on offer to buyers on a dark web marketplace
The dark web isn’t only a place to solicit new business in the criminal underworld, it’s also a space for learning as cybercriminals turn to dark web forums to discuss new tactics and developments in malware.
Criminals have been found discussing which large language models are best for running phishing attempts and which were more suited for coding malware. Etay Maor, chief security strategist at security platform Cato Networks, says attackers could be found on Russian-language forums discussing WormGPT, which they claim is the first generative AI-powered malware. Although it was found to be functionally useless.
On these forums, the dark web has become a new recruitment platform for those with machine-learning skills, introducing a new competitor in the search for people with these highly sought-after capabilities. This has left businesses, which are looking to hire those with the skills needed to master emerging technologies like GenAI, competing with cybercriminals for the same talent.
The cybercrime skills gap
For many legitimate security professionals, their jobs are increasingly thankless. A recent report from from defence thinktank RUSI, found that blame is often heaped onto cybersecurity workers when something goes wrong and, in the event of an attack, have reported facing subequent long hours, fatigue and even PTSD-like symptoms. With legitimate infosec professionals reporting burnout and poor job prospects, some are turning to dark web forums to find work, according to cyber industry group CIISec.
“We’ve seen several groups, including notorious ransomware gang Lockbit, looking to hire people,” adds Maor. “They list the technical capabilities they’re looking for on dark web forums and Telegram channels.” More worrying still, these potential recruits aren’t necessarily leaving legitimate jobs for illicit ones, they are doing both at once. “We’ve seen insiders advertising the access they have, including at major telecoms companies,” Maor continues.
“At the end of the day, people have to put food on the table,” he says. “When there are conflicts in the world like Russia-Ukraine, people lose jobs. You’ll see people pop up saying: ‘I know how to do X or I’ve been an employee of company Y’, and they’ll be recruited.”
How business leaders can use the dark web
There are many ways executives from across a business can use the dark web to improve their operations. Marketers can use it to gain valuable information on what counterfeits of their products look like, while CISOs can draw insights from discussions on emerging threat models.
For companies that are curious about the methods criminals are using to subvert existing software or exploit vulnerabilities to attack businesses, discussions on the dark web might provide a hint. Maor gives the example of the LockBit cybercriminal group, which re-engineered a free tool created by the cybersecurity company Kaspersky to disable the Windows Defender antivirus software on the machines of their victims.
Just as the FBI and CIA regularly scour black-hat hacker events for cyber talent, HR leaders at legitimate organisations could find highly skilled, innovative and technical talent on the dark web, Frankel suggests.
Insider threats and more: lessons on people and processes
The most important lesson for IT leaders should be to look inwards at their own people and processes.
Cyber threats such as ransomware are not going away. While organisations can search the dark web for signs of a potential attack, it’s nearly impossible to monitor every potential source.
Therefore, understanding the prevalence of access brokers across the dark web, many of whom automate the discovery of weak points in corporate networks, should encourage cyber leaders not only to secure their own perimeter but work to audit business partners and secure their entire supply chain.
Noting the increase of security professionals taking on criminal work on the side, organisations would do well to institute zero-trust access management policies, ensuring that individuals only have access to what they need in order to do their jobs. “The weakest link is usually people, from insider threats through to an employee clicking a malicious link and someone getting a foothold into your company’s internal networks,” says Mantas Sasnauskas, head of security research at Comparitech.
That means ensuring security has buy-in at every level of the organisation, while also making certain that data-handling policies abide by security frameworks such as NIST and ISO 27001. “As a great meme notes, hackers don’t care about your policies,” says Sasnauskas. “So you need to see if your policies and procedures are actually working.”
Businesses should also learn to treat their staff well. The fact employees in cyber are increasingly feeling under-valued, over-worked, under-paid and burned out should be a cause for concern. Businesses that treat their staff better are more resilient too, recent research has found.
While the dark web might seem off-limits for those leading legitimate businesses, there are crucial lessons to be learned from these underworld digital spaces.
The hidden dark web infrastructure behind a ransomware attack
The rise of ransomware-as-a-service means cybercriminal gangs are getting increasingly professional. Here’s a glimpse into how they work
When a ransomware attack occurs, a chain of events in the lead-up to the attack will determine whether it’s successful.
Attackers are rarely lone wolf types. Ransomware gangs are organised, professional operatives that rely on hierarchy, structure and their own supply chains.
With the move to the ‘as-a-service’ model, criminal groups became centralised and more sophisticated. They are now professionalised to such a degree that the organisation of these groups mirror those of legitimate businesses, says Mantas Sasnauskas, head of security research at comparison site Comparitech.
Senior figures take on roles similar to those in the C-Suite. Some cybercrime groups, such as Conti and its successor Lockbit, even have human resources-style development initiatives such as employee-of-the-month schemes.
When ransomware groups execute their attacks they rely on their own supply chains. Operators typically oversee the plan in a similar way to project managers. Their affiliates will hack into targets to spread ransomware and exfiltrate data.
Crucially, ransomware operators often rely on ‘initial access brokers’ – individuals who search for footholds within organisations, whether through running networks of bots to find entry points or by leveraging so-called insider threats, malicious agents within businesses, who are willing to let attackers in.
Would-be collaborators or attackers might find cybercrime groups on the dark web, such as on Tor, or on quasi-clearnet channels such as Telegram.
Usually, says Sasnauskas, these forums or channels are in Russian, but translation tools make navigating them simple for anyone.
“A lot of these forums forbid ransomware adverts, but obviously new forums spring up where they can be placed,” says Sasnauskas, who has infiltrated ransomware groups himself.
He adds: “The adverts on these forums literally say, ‘if you can penetrate a network, or hack a company, we will provide you with the tools or malware you need to encrypt important files and steal what’s important.’ You don’t need to do anything else.”
The operator then takes care of the rest. They demand the ransom, arrange the payment and take their cut.

The ‘dark web’ isn’t only the home of illicit marketplaces for drugs and weapons, although those can certainly be found. It is also becoming a crucial recruitment platform for gangs of cybercriminals.
As the infrastructure behind ransomware-as-a-service becomes ever-more professional and sophisticated, the dark web – unlisted websites only accessible via encrypted technologies like the Tor network – is an important space to understand how cyber attackers tick. For businesses, it can offer valuable insight into how criminal gangs are targeting white-collar IT professionals and why they are succeeding.




